Monitoring and managing vulnerabilities in embedded Linux devices presents a unique set of needs that traditional IT vulnerability tools fail to address and result in wasted efforts chasing false positives and inefficiencies due to cumbersome workflows. After evaluating multiple IT cybersecurity tools, we at Timesys ended up creating a vulnerability management tool called Vigiles, which is optimized for embedded devices. This blog aims to share the lessons learned and how the right tool can bring your security maintenance cost down while improving the security posture of the device.
Open Source Embedded Software Development and Security Blog
Ready to tackle embedded Linux MPU development with Windows … Do you know your options?
Have you been developing embedded devices for years? Are you considering building your first operating system based product and looking at using embedded Linux? You are not alone.
Many companies that have historically been developing MCU based products are now being pushed by market and customer requirements to offer better, more feature-rich and more capable devices. In order to deliver the desired features, many new designs require a …
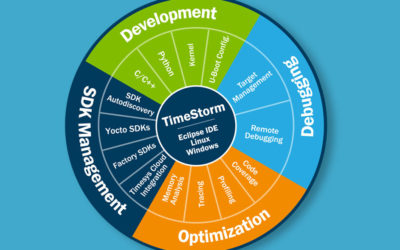
Why choose TimeStorm IDE over standard Eclipse for embedded Linux development?
As the product manager for TimeStorm, I am often asked the following two questions about TimeStorm, our Integrated Development Environment (IDE):
- Why would I need an integrated development environment?
- What can I do with TimeStorm that I can not do using Eclipse with available open source plugins?
There is no simple answer to these questions. Or is there?
Managing vulnerabilities: The importance of security notification and how to leverage Timesys’ solution
Security Is Important
No matter what industry you’re in, maintaining the security of your software is vital. It may be obvious that medical devices need to protect patients and their privacy, but a range of consumer gadgets fueling the IoT have also been targeted and used to cause real damage.
Meltdown and Spectre vulnerabilities
Google Project Zero team discovered a method to read privileged memory from user space by utilizing CPU data cache timing to leak information out of mis-speculated execution. Variants of this issue are known to affect many modern processors, including certain processors by Intel, AMD and ARM. For more details refer to this blogpost.
Secure Boot and Encrypted Data Storage
Secure boot ensures only authenticated software runs on the device and is achieved by verifying digital signatures of the software prior to executing that code. To achieve secure boot, processor/SoC support is required. In our experience, some of the more secure boot friendly processors with readily available documentation are NXP i.MX, Xilinx Zynq, and Atmel SAMA5 series. Some TI Sitara processors support secure boot, but might involve TI factory programming of signing keys and custom part numbers.
Securing Embedded Linux Devices
Embedded devices have unique security needs ranging from IP protection, anti-cloning / anti-counterfeit capability, device software integrity, user data protection, securing network communication, device authentication and ability to run only trusted applications. A wide range of open source technologies are available that can help implement the aforementioned security requirements. However, it is not always apparent which mechanisms are best suited for a given use case, resulting in a steep learning curve. This blog series aims at giving a high-level overview of the different methods to secure your product and help accelerate your trusted software deployment.
Software / Firmware Update Design Considerations
The Internet of Things (IoT) has quickly led to the deployment of ubiquitous, unattended devices throughout our homes, offices, factories and public spaces. In this continuously expanding connected world of devices and IoT, the need to update/upgrade your product’s software/firmware is a certainty. There is no single software update approach that fits all, but there are key questions you should consider when designing your approach. They are: Why, When, What and How.