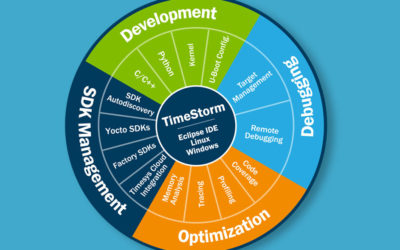
As the product manager for TimeStorm, I am often asked the following two questions about TimeStorm, our Integrated Development Environment (IDE):
- Why would I need an integrated development environment?
- What can I do with TimeStorm that I can not do using Eclipse with available open source plugins?
There is no simple answer to these questions. Or is there?