From customer expectations to cybersecurity regulations, the demand for security assurance of devices has never been greater. Yet device manufacturers find it challenging to secure Linux devices. Establishing a secure Linux platform requires deep expertise and time...
Open Source Embedded Software Development and Security Blog
VigiShield Secure By Design for Yocto
Overview The Yocto Project is a popular choice for creating custom Linux distributions for IoT devices. When creating a custom Linux distribution one of the key challenges faced by device manufacturers is the time and expertise required to secure the distribution....
Yocto Security: Automating compliance using OpenSCAP
The Security Content Automation Protocol (SCAP) is a method of using certain interoperable security standards to automate evaluating policy compliance of deployed systems. In order to scan a system for compliance or vulnerabilities, there are two components involved:...
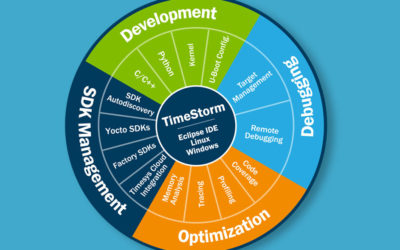
New IDE version produces shorter time-to-market for secure IoT devices and embedded Linux applications
This week we announced a new release of our TimeStorm Integrated Development Environment (IDE). TimeStorm 5.3.2 IDE is designed to streamline, simplify and accelerate the development of secure Internet of Things (IoT) and embedded Linux applications.
In an era of heightened awareness of embedded software security and device security risks, product developers need to be able to adopt security best practices without delaying the development and release …
Monitoring and managing vulnerabilities for embedded systems built with Yocto
The Yocto Project is well known for enabling product developers to quickly and easily customize Linux for Internet of Things (IoT) devices and other embedded systems. But today’s environment is marked by heightened security concerns, skyrocketing vulnerability reports, and high-profile security breaches.
Getting your embedded system product to market fast is important. But getting to market fast without a secure design and a plan for managing future vulnerabilities is a huge mistake.
Managing vulnerabilities: The importance of security notification and how to leverage Timesys’ solution
Security Is Important
No matter what industry you’re in, maintaining the security of your software is vital. It may be obvious that medical devices need to protect patients and their privacy, but a range of consumer gadgets fueling the IoT have also been targeted and used to cause real damage.