Security Feature Implementation
VigiShield Secure by Design
Build security into the design of your device by utilizing our embedded experts to implement core security features. This includes: secure boot/chain of trust, device encryption and secure key storage, Over-the-Air (OTA) software updates, hardening, and security audits.
Implementing security early in the design of your device is key to managing its security:
- Reduce the attack surface of your device
- Avoid production delays by securing your software supply chain


Vulnerability Monitoring and Remediation
Vigiles
Manage the growing tsunami of new CVEs (Common Vulnerabilities and Exposures). Detect, filter, triage, and remediate vulnerabilities with the industry’s first Software Composition Analysis (SCA) and CVE monitoring tool optimized for embedded Linux and usable for all open source software.
- Drastically reduce your workload
- Produce an accurate Software Bill of Materials (SBOM)
Long-Term Support
Linux OS and BSP Maintenance
Keep your device secure while in the field with long-term security updates & maintenance. Offload the complex, time-consuming work of OS/BSP maintenance to embedded Linux security experts.
- 60%+ cost reduction for BSP maintenance
- Updates based on your schedule, as often as you need them
- Long-term support for up to ten years and beyond

Embedded Linux/Android OS and BSP Development
Engineering Services and Consulting
Work with embedded platform experts with broad experience across Linux, Android, and RTOSes to help build and secure your custom embedded platforms and custom BSPs. Timesys can help with: custom board bringup; device driver development; kernel upgrade; boot time improvement and performance tuning; manufacturing support for End-of-Line (EOL) Test and programming devices; and more.
- Broad expertise in embedded OS & build systems
- Engage at any stage of product lifecycle
- Work with industry pioneer: founding member of Yocto Project
Test Automation and Remote Access Infrastructure
Embedded Board Farm
Utilize our test automation infrastructure to bring your embedded device into your CI/CT process. Make your boards remotely accessible for collaborative software development, test automation, and debugging from anywhere in the world.
- Use a modern CI/CT system to achieve higher efficiency and quality
- Integrate your favorite test framework onto shared board farm infrastructure, with real hardware
- Minimize cost and project schedule by eliminating hardware access bottlenecks

SEE THE SOLUTION YOU NEED?
Start the Conversation
Stop worrying about how you are going to find the engineering time and in-house expertise to give your product the professional architecture and security attention it needs.
Development Tools
Embedded Linux IDE
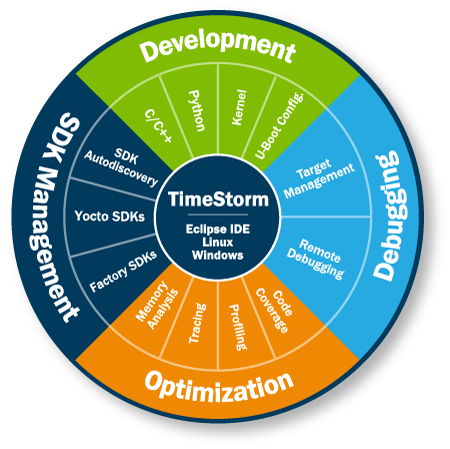
TimeStorm
Integrated Development Environment (IDE) optimized for embedded Linux application & system development.
- Powerful suite of integrated tools for embedded Linux that enables application developers to quickly and easily create complex applications.
- Optimizes the application developer’s workflow and makes it easy to code, debug and maintain complex applications.
- Expertly handles embedded development chores like multithreaded application debugging, kernel configuration, cross-compiling and remote debugging while including support for advanced features like profiling, tracing and memory leak detection.
Embedded Linux Development and Customization
Factory
Timesys Factory Embedded Linux BSP and SDK Build System allows developers to create custom BSPs easily and quickly.
- Graphical, embedded Linux build system.
- Offers optimized workflows and “cleaned,” preconfigured BSP components.
- Open source tool suite available either in desktop or cloud configurations.
Support and Training
As-Needed Support Subscription
Engineering Development Support
Get development engineering support for your embedded Linux distribution and custom Board Support Package (BSP) for a fraction of the cost of a full-time engineer.
- Project-based engineering support including:
- Development setup, continuous integration setup issues
- Cross-compilation, configuration and build-time issues
- Analysis of run-time issues
- Expert, responsive team of Linux engineers
- Dedicated support engineers
- 24 hour initial response time
- Support for Factory, Buildroot, and Timesys Factory
- Self-help & education
- Extensive documents, videos, demos, and webinars
Two Day Hands-On Introductions
Jump Start Training
Timesys Jump Start is a customized 2-day course with hands-on exercises based on your application requirements. Our training courses are designed to help get you and/or your team up and running quickly.
Get Jump Start training in:
- Embedded Linux
- Yocto Project development
- Security
SEE THE SOLUTION YOU NEED?
Start the Conversation
Stop worrying about how you are going to find the engineering time and in-house expertise to give your product the professional architecture and security attention it needs.
