Vulnerability Management for Embedded:
SCA Tool Evaluation Checklist
Guide to evaluating vulnerability tools for embedded Linux devices
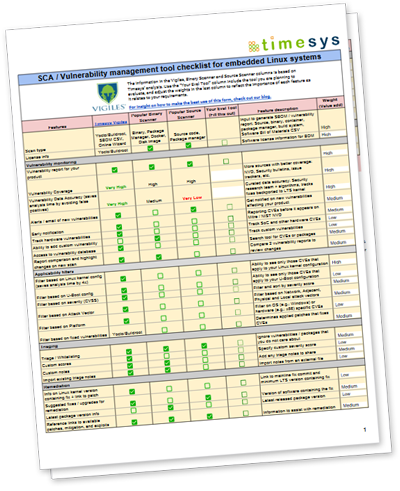
Monitoring and managing vulnerabilities for embedded Linux products requires a range of unique functions and capabilities in Software Composition Analysis (SCA) tools.
Timesys has compiled an evaluation checklist that delineates the required features and provides details to aid in the evaluation of SCA tools. The checklist also provides a comparison of binary scanners and source scanners with Timesys Vigiles in relation to the requirements.
Requirements covered include:
- Vulnerability monitoring
- Filtering
- Triage
- Remediation
- Collaboration and reporting
Fill out the form to download the checklist today.
Unable to see this form? Please disable any tracker blockers you may have turned on. Or if you don’t want to turn off your tracker blocker, just email sales@timesys.com, and we’ll fill out the form on your behalf.
* Denotes required field.
