Secure by Design: Developing more secure connected embedded systems
Cybersecurity of connected embedded system devices has always been important, especially for systems supporting high availability, mission-critical applications.
In today’s heightened cyber threat environment, connected embedded systems for industrial controls, transportation, navigation, communications, aerospace, military applications, healthcare devices, logistics systems and many others require uncompromising security at deployment and throughout their product lifecycles.
For more than 20 years Timesys has been the industry’s trusted partner for secure embedded software design and development. We provide device makers and system developers with tools and services to accelerate time to market of more secure products.
Secure by Design: Developing more secure connected embedded systems
Cybersecurity of connected embedded system devices has always been important, especially for systems supporting high availability, mission-critical applications.
In today’s heightened cyber threat environment, designing connected devices with the strongest possible security posture is essential. Embedded systems for industrial controls, transportation, navigation, communications, aerospace, military applications, healthcare devices, logistics systems and many others require uncompromising security at deployment and throughout their product lifecycles.
For more than 20 years Timesys has been the industry’s trusted partner for secure embedded software design and development. We provide device makers and system developers with tools and services to accelerate time to market of more secure products.
Building secure products
Timesys’ embedded system development tools and services provide you with the industry’s best practices for Secure by Design, for building and maintaining secure connected embedded systems.

Compliance assistance with regulatory and government security requirements: US FDA Guidance, EU Cybersecurity, IEC 62304, SCADA, other security specifications

System hardening, secure boot, encrypted storage, trusted execution environments, high availability, for ruggedized and highly secure applications

Vulnerability detection and mitigation tools, secure incorporation of third-party components, automatic software patch and update notifications
Securing the software supply chain

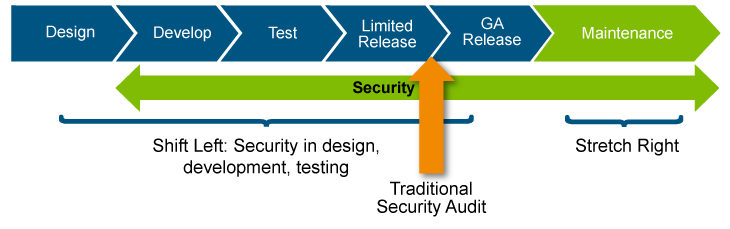
Security shifts left and stretches right
Have a project you’d like to discuss?
Fill out the form for a no-obligation consultation about your connected embedded system project. We offer best-practices guidance on:
- Secure boot and encrypted data storage, two foundational security functions to be considered in embedded system design.
- Securely incorporating third-party software into your products.
- Deploying a Trusted Execution Environment (TEE) to reduce risk associated with third-party software.
- Software / Firmware Update Design Considerations, including Over-the-Air (OTA) updates.
- Device hardening.
- Device security audits.
- Vulnerability monitoring and mitigation.
* Denotes required field.

