Security Simplified
Need help implementing internal cybersecurity requirements or meeting industry standards?
Looking to collaborate with security experts to bring in best-in-class technologies to secure your devices?
Need help implementing internal cybersecurity requirements or meeting industry standards?
Looking to collaborate with security experts to bring in best-in-class technologies to secure your devices?
With VigiShield Secure by Design, we’ve distilled the security feature implementation process down into an easy-to-understand security layer that can be configured to meet your current customer and regulatory (e.g. NISTIR 8259A and ETSI EN 303) requirements.
VigiShield leverages widely used open source technologies, enables underlying hardware capabilities for best performance, and implements the security best practices recommended by regulatory and industry-specific bodies (FDA, IEC, etc).
With security built-in using VigiShield, device manufacturers can focus more on innovation during the product development process and get to market faster.
| Requirement | VigiShield Secure by Design* | ETSI EN 303 645 | NIST 8259A | SB-327 |
|---|---|---|---|---|
| Authentication/Password | x | x | x | x |
| Configuration | x | x | ||
| Crypto | x | x | x | |
| Hardening | x | x | x | |
| Logging | x | x | ||
| Secure Storage | x | x | x | |
| Update | x | x | x |
* PSA Certified Level 1 Version 2.0
Take advantage of our embedded security expertise.
For more than 20 years, Timesys has been the industry’s trusted partner for secure embedded software design and development. We provide device makers and system developers with tools and services to accelerate time to market and develop more secure products.
VigiShield Security Features
Prevent Firmware Tampering
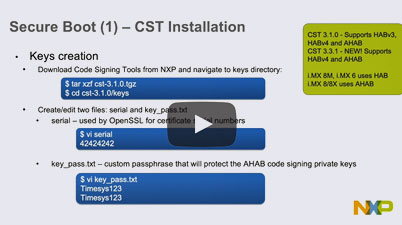
Secure Boot / Chain of Trust
Ensure your device is not running tampered software by verifying its authenticity before execution. Establish software authenticity all the way from the bootloader to user applications by implementing:
- Verified bootloader (NXP i.MX / QorIQ, Qualcomm Snapdragon, TI Sitara, Atmel SAMA5, Xilinx Zynq, NVIDIA® Jetson™, STM32MP1, Intel® x86 and Atom™, etc.) integrated with Yocto, Buildroot and more
- Linux kernel verification (FIT image, SoC specific mechanisms)
- Root filesystem verification (dm-verity, FIT image)
Keep Your IP and User Information Safe
Device Encryption and Secure Storage
You can protect IP and sensitive user information by encrypting data/software. It is also critical to protect the key used for encryption using a secure storage mechanism. Additionally, software that handles confidential data should run from within a hardware/software-isolated environment. We provide:
- Anti-cloning (IP and Data Protection)
- Key management and secure key storage
- Data protection using encryption — In use, in motion, and at rest
- Trusted Platform Module (TPM)
- Device identity and authentication
Keep Your Updates Safe
Secure Software Updates
Our solution provides a mechanism to update/deploy software securely and deny unauthorized software installs. We provide:
- Over-the-air (OTA) updates of the software on your embedded system
- Package updates
- Full OS updates
- Signing of packages and images
- Server authentication
- Prevention of unauthorized rollback

Keep Your Data In Transit Secure
Secure Communication
Ensure the connection from the device to the cloud and/or any external devices is protected. VigiShield secures device communication:
- Authenticated and encrypted connections
- Protection of device certificates/keys
- Use best-in-class ciphers
Keep A Paper Trail
Security Audit Logs
Record any runtime security violations/breaches on the target system. VigiShield has:
- Encrypted audit logs with user authentication
- Customizable policies for recording security incidents

![]()
Lock It Down
Hardening
Our Linux kernel hardening service focuses on system configurations needed to reduce your product’s attack surface, decrease risk of compromise, and minimize breach impacts including:
- Access and authorization
- Vulnerabilities
- Logging of all user access
- Logging of access level changes by any program
- Disabling unused services and ports
- Addressing issues from penetration testing reports
- Security-oriented configurations for packages and kernel
Know Where Your Software Comes From and Stay Resilient
Software Supply Chain Security
VigiShield Secure by Design helps you gain visibility into your software supply chain and secure it by:
- Choosing the right open source software
- Implementing end-to-end framework for supply chain integrity
- End-to end-review of system security
- SBOM and vulnerability report
![]()
VigiShield Add-Ons
Yocto/BSP and Security Customizations
Apart from the standard PSA certified VigiShield offering, we provide customizations as part of our Professional Services which covers hardware enablement, Yocto customizations, custom security feature implementations, address issues from penetration testing reports, integration with device management / IoT cloud services, and more!
Out-of-the-box Container Support
Support legacy apps with outdated dependencies, improve productivity by decoupling app development from the platform development schedule, and improve portability and updatability with this container support add-on that ensures app containers can run on different hardware and OS platforms, and be updated without needing to update the base OS. This add-on additionally offers boot time and image size optimizations, pre-integrated docker runtime support in the base OS, tooling to integrate the container into Yocto image, and more.
Security Training
Whether you are new to security, looking for consultation to refine your security requirements or help integrating our solutions into your processes; we can help with our customized security training offerings.
Trusted Applications for Secure OS
For customers seeking enhanced security and key provisioning, we have expertise in implementing “trusted applications” that can be deployed on a secure OS (e.g: OP-TEE, Trusty, etc) running on a trusted execution environment. Ensure your keys are never exposed and vastly reduce the attack surface of your applications by provisioning keys and certificates into the PKCS#11 compatible keystore.
Code-Signing Key Protection
For an additional layer of security, this ready-to-use tooling ensures your keys are never exposed outside of Hardware Security Modules (HSMs) by storing the code signing key on HSMs and requiring the build system to request signing using a PKCS#11 interface. With this feature, you can unify your key management across all products, simplify and standardize your signing process, and ensure that your devices meet compliance standards such as FIPS 140-2, Level 3. This includes signature support for bootloader, fitImage, dm-verity, and firmware update bundles and can easily be integrated into your CI/CD DevSecOps.
Secure manufacturing assistance
We have expertise in developing the manufacturing tooling required for secure software programming and provisioning. We can help integrate your custom or 3rd party solutions for securely storing device certificates.
Manufacturing Protection for i.MX8 and i.MX9
To further help you securely build devices at contract manufacturing facilities and prevent counterfeit attempts, this VigiShield add-on enables you to detect unauthorized production, protect your IP at manufacturing facilities, verify your processors, and ensure SoC authenticity. On networked devices, you’ll be able to authenticate the device with a provisioning server using i.MX manufacturing protection keys. For non-networked devices, encrypt your secrets using i.MX manufacturing protection keys and bundle them with the production image.
Long Term Linux OS security and maintenance
Timesys Linux OS/BSP Maintenance subscription service provides long-term security updates and maintenance of your Linux OS. Using this service, device manufacturers can rely on timely security updates that can be deployed to devices in the field with the secure and robust OTA update mechanism included in VigiShield.
System Security Audit and Review
By performing a risk analysis, our audit services can help you determine what potential threats your system might encounter and what should be secured.
VigiShield
|
|
|---|---|
| PSA Certified | NXP i.MX8 |
| ST STM32MP SoCs | |
| NXP i.MX6 | |
| NXP QorIQ | |
| Xilinx Zynq, Ultrascale+ | |
| NVIDIA Jetson | |
| Qualcomm Snapdragon | |
| TI Sitara AM6xx | |
| Microchip/Atmel SAMA5 | |
| Intel x86 and Atom |
![]()
Reduce the attack surface of your device
Improve the security posture of your device by auditing, hardening, optimizing your software footprint, and implementing secure boot and chain of trust.
![]()
Avoid production delays by securing your software supply chain
Avoid the rework and cost overruns that come with deploying security too late in design. Leverage detailed SBOMs and an end-to-end framework to ensure the integrity of your software supply chain.
SEE THE SOLUTION YOU NEED?
Start the Conversation
Stop worrying about how you are going to find the engineering time and in-house expertise to give your product the professional architecture and security attention it needs.