The content of this blog has been recently updated to reflect features and functionality that have been added to Timesys’ Vigiles Vulnerability Monitoring and Management.
Security Is Important
No matter what industry you’re in, maintaining the security of your software is vital. It may be obvious that medical devices need to protect patients and their privacy, but a range of consumer gadgets fueling the IoT have also been targeted and used to cause real damage.
When security is an afterthought and products are near release, and especially when they are already in the field, addressing vulnerability issues becomes a lot riskier and much more costly. This is one reason that we advocate for designing with security in mind from the beginning. Since most open source vulnerabilities are fixed by upgrading to a new version or applying a patch, it’s important to make scanning for Common Vulnerabilities and Exposures (CVEs) and applying their fixes a regular part of the development process.
The Challenge with Monitoring CVEs Yourself
Thousands of CVEs that are published every year affect open source software, including the Linux kernel and other software that your products depend on (from down in the C Library, to video codecs, and up through web servers). In fact, some CVEs may even affect the very components designed to make your product more secure in the first place (e.g. libgcrypt / GnuPG or OpenSSL).
Continuously monitoring security databases and mailing lists for vulnerabilities is time-consuming work. Every day you need to keep up with newly issued notices to make sure you do not miss anything for any component included in your system. Keeping this up manually is an enormous challenge, and yet there is still more work to do. What do you do with that information? Your time would be better spent determining the real impact each CVE potentially has on your product, and taking the corrective action. Is it a component your application uses? If not, can it be disabled at build or run time? If it is used, should you move to an updated version, or patch it? And do you need to backport the fix, or is a patch already available for your version? How will you test it once it’s applied? What about deploying it?
The Timesys Solution
Timesys helps reduce the time and costs associated with maintaining software security through its automated Vigiles® Vulnerability Management Suite.
Monitoring
Our team of security experts, the Timesys TRST team, constantly monitors security issues that impact open source software being used by our customers, proactively updates the Factory repository with patches and updates, and maintains Yocto patches and updates for recipes across multiple Yocto releases.
Notification
We have developed tools for Yocto, Buildroot and Factory, for both the desktop and web, which make tracking relevant security vulnerabilities easy. Since we do the monitoring, all you need to do is consume the notifications.
Subscribers can generate a report on-demand using the current build configuration for up-to-date notification that is relevant to the build. Whether uploaded on the web initially, or checked from the command line, those configurations and reports will also be stored in your Vigiles account within the LinuxLink portal. This allows you to see how the threats to your product are changing over time. Customers can optionally choose to subscribe to notifications for any configuration, which will have a new report generated and emailed weekly.
Patching
To address the CVEs, Timesys provides patches, which will be discussed more in depth in future blog posts.
How to Use It
Yocto Project images
A few easy steps is all it takes to try on-demand notifications for Yocto using the meta-timesys layer. To use subscription and history features, you will also need to set up your LinuxLink API Keyfile. If you don’t have a subscription, only a short summary will print to the console. You can still view the full report online with a free account, but without a subscription, reports will not remain accessible for more than one day.
The instructions below pull meta-timesys and poky to set up a minimal Yocto environment for demonstration purposes. Feel free to try inserting meta-timesys into your own BSP as well. It supports custom machines, distros, and images just fine!
- Clone meta-timesys into your Yocto source directory
git clone https://github.com/TimesysGit/meta-timesys.git -b master
- Include meta-timesys in bblayers.conf (modify path as needed)
BBLAYERS += "${TOPDIR}/../meta-timesys" - Inherit Vigiles in local.conf by adding the line below:
INHERIT += "vigiles"
- Download a LinuxLink API key from here, and store it in the path below:
/home/<user>/timesys/linuxlink_key
Note: If the key is stored elsewhere, then specify the full path in local.conf. e.g:
VIGILES_KEY_FILE = "/tools/timesys/linuxlink_key"
- Run bitbake <your-image-name>.
$ bitbake core-image-minimal
A manifest is automatically generated and uploaded to Vigiles, and a link to a vulnerability report is provided in the command line output. By default the manifest is uploaded to the “Private Workspace” under your Vigiles account.
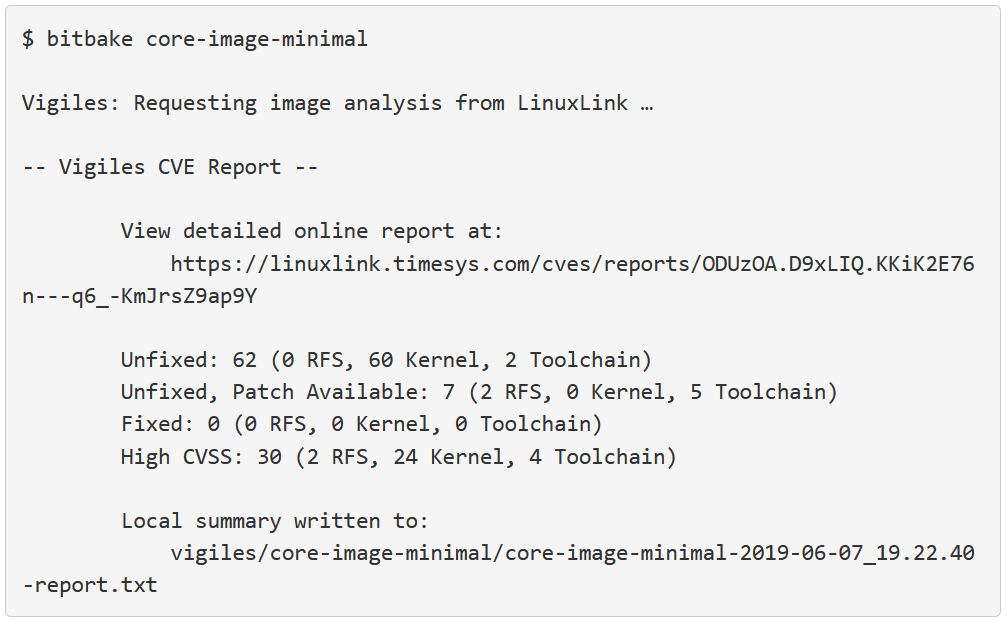
Sample Report
You can view a full sample report online here.
Buildroot images
To try on-demand notifications for Buildroot using vigiles-buildroot, simply follow the four steps as outlined below. To use subscription and history features, you will also need to set up your LinuxLink API Keyfile. If you don’t have a subscription, only a short summary will print to the console. You can still view the full report online with a free account, but without a subscription, reports will not remain accessible for more than one day.
- Clone vigiles-buildroot repository at the same level as Buildroot directory.
git clone https://github.com/TimesysGit/vigiles-buildroot
- Download an API key from here and store it in the path below:
/home/<user>/timesys/linuxlink_key
Note:If the key is stored elsewhere, then use the menuconfig option to specify the correct path.
- Export the path to vigiles-buildroot using the following command:
make BR2_EXTERNAL=/path/to/vigiles-buildroot menuconfig
Note: If you already have a custom external buildroot tree, then export both paths. e.g.:
make BR2_EXTERNAL=/path/to/vigiles-buildroot:/path/to/custom menuconfig
- Run the vigiles check command.
make vigiles-check
A manifest is automatically generated and uploaded to Vigiles, and a link to a vulnerability report is provided in the command line output.
- View the Vigiles CVE (Text) Report Locally or Online. The CVE report will be located in the vigiles/ subdirectory of your Buildroot build output.
wc -l output/vigiles/buildroot-imx8mpico-report.txt 3616 output/vigiles/buildroot-imx8mpico-report.txtThe local CVE text report will contain a link to a comprehensive and graphical report; e.g.:
-- Vigiles CVE Report -- View detailed online report at: https://linuxlink.timesys.com/cves/reports/< Unique Report Identifier>
Sample Report
You can view a full sample report online here.
Factory
With an active subscription and your LinuxLink API key set, a recent Desktop Factory will run the cvecheck by default when you run make, or by running either of the following targets:
- make checkupdates
- make checkcves
The checkupdates target also provides information about any newer Factory version and what updates it has for your selected packages (including CVE fixes). The CVE results in any case break down into the following categories:
- Unfixed — Known to affect the package at this version, which no solution available at this time
- Unfixed, Patch not Applied — A fix is available in the local Factory, but it hasn’t been applied to your workorder. Usually this means you should run make menuupdate and accept the new patch list.
- Unfixed, Upgrade Available — Can be fixed by upgrading to a newer Factory which provides an updated version or a patch.
- Fixed — Known to affect the package this version, but already fixed or mitigated by a patch applied in the Workorder.
You can view a full sample report online here. To subscribe for notifications, enable the option in the Workorder using make menuconfig under the “Advanced Build Configuration” menu, and then run any of the commands that trigger a report (make, make checkupdates, make checkcves).

LinuxLink Web
The Vigiles dashboard is where you will find stored Yocto, Buildroot, and Factory configs (referred to in Vigiles as manifests) as well as any custom manifests (.csv) you have manully uploaded, view past reports, generate new reports on-demand, and manage subscription settings for push notifications via email. By default, Yocto, Buildroot and Factory CVE reports generated via command-line are automatically stored in your Private Workspace within your Vigiles account.
When you log in to LinuxLink, click on the “Vigiles Dashboard” tile or on the “Vigiles” menu item in the top navigation, then navigate to a product folder and select the manifest for which you want to view the vulnerability report. A demo version of a vulnerability report is available. If logged in to LinuxLink,
A demo version of a vulnerability report is available here. If you are already logged in to LinuxLink, you’ll be redirected to your Vigiles dashboard, so make sure you are logged out if you want to view the demo report (shown below).
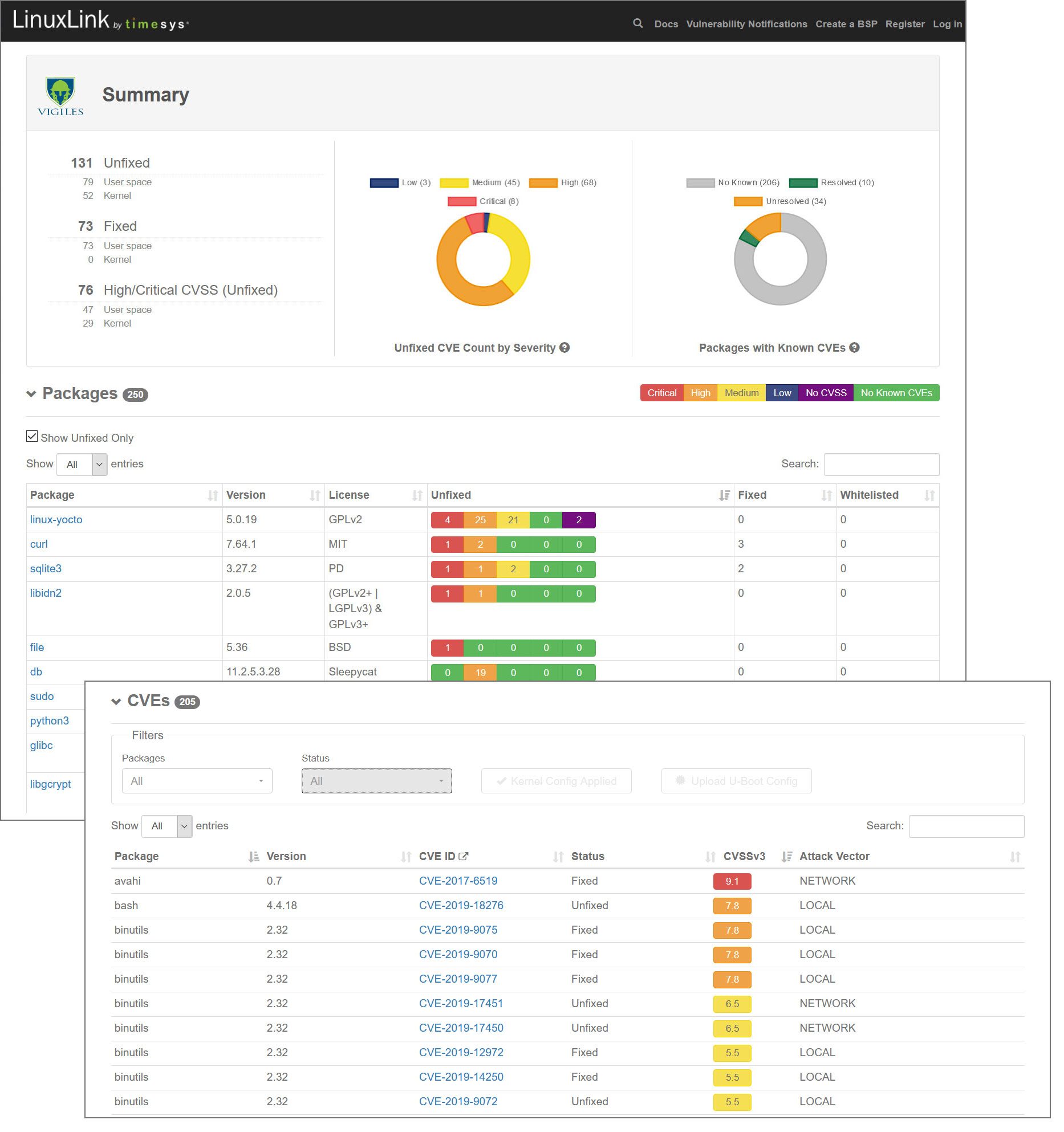
The most recent report for a manifest can be accessed by simply clicking on the manifest name or you can view all reports for a manifest by clicking on the ALL link located in the CVE Reports column in the same row as the manifest name.
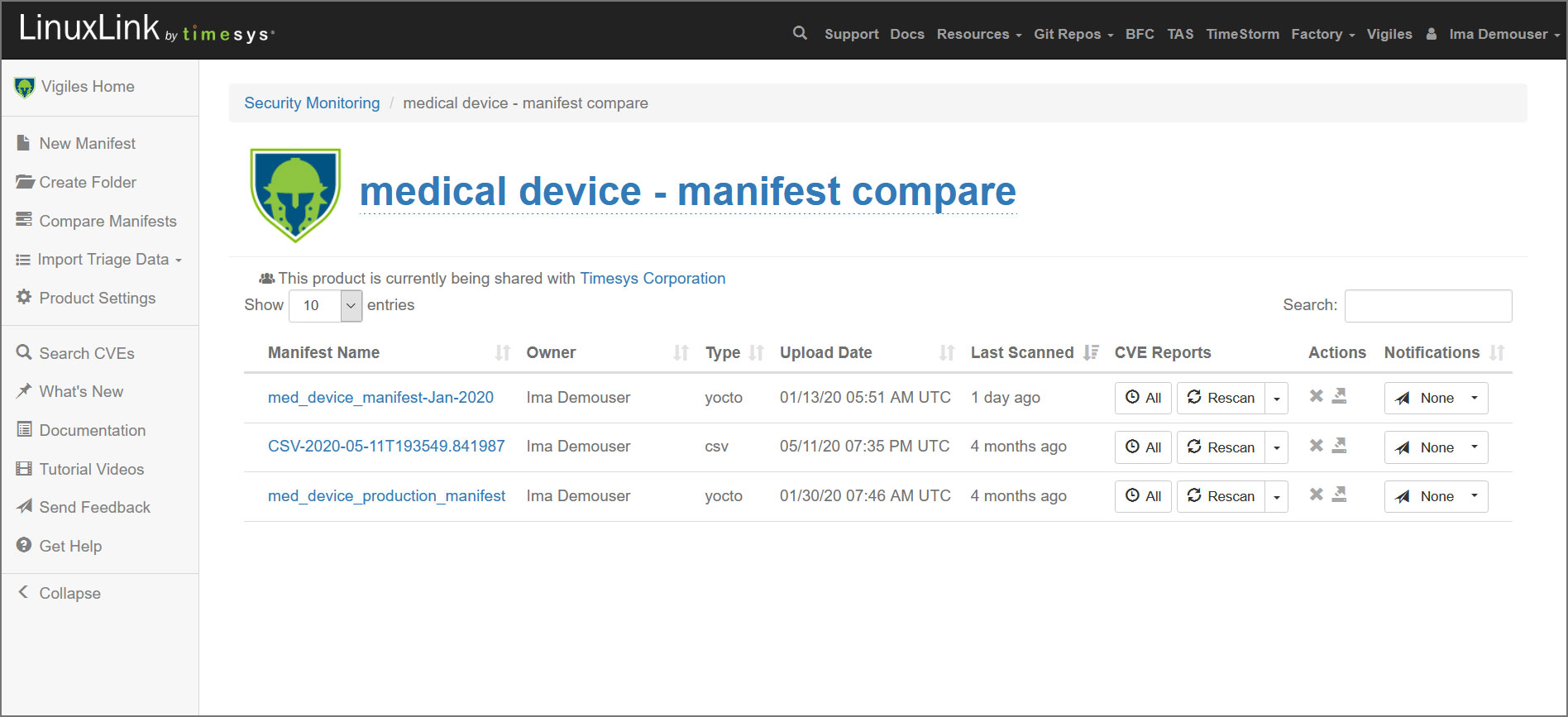
To submit a config online, you can click the New Manifest button from within any Product folder including your Private Workspace folder and submit a Yocto Image Manifest (created with meta-timesys), a Buildroot manifest (created with vigiles-buildroot), a Factory Workorder or a custom (.csv) manifest. Once the manifest has been uploaded, Vigiles will automtically scan it and take you to the initial CVE report.
From the Notifications dropdown, which you’ll find to the right of each manifest in your product folders, you can set your pull notification cadence or turn off pull notification altogether.
About Timesys
Timesys has extensive experience with embedded system development and lifecycle management. Timesys has been instrumental in working with global leader semiconductor manufacturers with smart, quick and quality solutions for highly complex systems with accelerated product innovation and multiple product variants.

