Responding to Recent Attacks with Vigishield In light of recent attacks on the open source community, we've been asked if or how our tools (specifically, Vigishield) could have helped prevent them from being successful. The two most recent attacks of interest were:...
Open Source Embedded Software Development and Security Blog
Securing Your Software: Generating SBOMs from Linux Binaries and Scanning for CVEs Without Source Code
Why Scanning for CVEs is Essential in Open Source Software Maintenance Scanning your open source software for CVEs (Common Vulnerabilities and Exposures) is a very important maintenance step for any software project. Generally, these CVEs are stored in publicly...
Designing Yocto platforms for scalability and maintainability across product lines
Scaling software development is a perennial problem. As product lines grow, maintenance costs for device manufacturers can increase dramatically when software is ported and reused from one product to the next. This can balloon into major issues like security...
VigiShield Secure By Design for Yocto
Overview The Yocto Project is a popular choice for creating custom Linux distributions for IoT devices. When creating a custom Linux distribution one of the key challenges faced by device manufacturers is the time and expertise required to secure the distribution....
Yocto Security: Automating compliance using OpenSCAP
The Security Content Automation Protocol (SCAP) is a method of using certain interoperable security standards to automate evaluating policy compliance of deployed systems. In order to scan a system for compliance or vulnerabilities, there are two components involved:...
The many challenges of Linux OS / BSP security maintenance
A recent blog post by Kees Cook, a Linux security expert and Google security engineer, illustrates the challenges in maintaining the security of the Linux kernel. One of the main takeaways from the blog is: “If you’re not using the latest kernel, you don’t have the most recently added security defenses (including bug fixes).”
Going the “upstream first” route is the absolute best way of keeping the kernel secure. However, it is only part of the story.
Evaluating vulnerability tools for embedded Linux devices
Monitoring and managing vulnerabilities in embedded Linux devices presents a unique set of needs that traditional IT vulnerability tools fail to address and result in wasted efforts chasing false positives and inefficiencies due to cumbersome workflows. After evaluating multiple IT cybersecurity tools, we at Timesys ended up creating a vulnerability management tool called Vigiles, which is optimized for embedded devices. This blog aims to share the lessons learned and how the right tool can bring your security maintenance cost down while improving the security posture of the device.
Best practices for triaging Common Vulnerabilities & Exposures (CVEs) in embedded systems: Top Three Questions Answered
Keeping embedded system products secure requires ongoing, constant monitoring and management of Common Vulnerabilities and Exposures (CVEs) throughout the production lifecycle.
With the constant flood of CVEs reported each week, you need to have a process for understanding the …
Vulnerability management and triaging
With 300+ vulnerabilities being reported weekly in the US National Vulnerability Database (NVD), it is more challenging than ever to maintain the security of open source and third-party software used in embedded system products. One common approach to tackle the problem is to adopt a risk-based vulnerability management strategy in which vulnerabilities that pose the highest risk to your organization are remediated first. This blog outlines how to establish such an process as part of your software development lifecycle while keeping the maintenance cost and risk of exposure low.
Webinar with NXP: CVE triage best practices for efficient vulnerability mitigation
Securing your embedded system devices is no longer just a final step in product development.
Security today must be a continuous process, a focus at every stage of your software development, release and maintenance cycles.
That’s because today’s vulnerability environment is radically different from the past. Hundreds of vulnerabilities that may or may not affect your …
Vigiles Quick Start … because securing your products doesn’t have to be hard
There is an old saying among cybersecurity vulnerability management practitioners:
The “good guys” have to get it right every time.
The “bad guys” have to get it right only once.
That means that the “good guys” — the security professionals whose mission is to keep corporate data safe — need to monitor, analyze and respond to every vulnerability that puts their systems, users and data …
BSP Lifecycle Maintenance: Top Three Questions Answered
Security is critical throughout the lifetime of an embedded system. Continually changing threat environments, new deployment modes and third-party software updates mean that the BSP software for an embedded system device can no longer remain static and “frozen.”
We explored embedded system security and best practices for maintaining a BSP throughout its lifecycle in a recent webinar with our partner NXP.
If you missed the webinar, be sure to catch the replay …
Vigiles Enhancements: Software Composition Analysis (SCA) & CVE Mitigation for Stronger Embedded System Security
A giant list of vulnerabilities does little to help you bring more secure products to market.
What matters is how you filter the list, triage the vulnerabilities, and mitigate the ones that pose the greatest risk.
That’s why the new enhancements to our Timesys Vigiles Security Monitoring & Management Service will …
Stop Chasing Vulnerability Ghosts: Why efficient vulnerability detection is essential to medical device security
To detect and correct vulnerabilities, eliminate false positives and prioritize the rest.
Every embedded system device maker should want to make security a selling point, preventing breaches or exploits, not an embarrassment if a security problem occurs. But nothing equals the liability and regulatory risk associated with medical devices.
Medical Devices: Automated Vulnerability Monitoring for Streamlined FDA Security Compliance
Reducing cybersecurity risks to medical devices is essential. Regulators like the US Food and Drug Administration (FDA) have made improving medical device security a critical focus in recent years.
This means many in the medical device manufacturing community are now rethinking how the software components of their products are secured throughout their product lifecycles.
NXP Solves Vulnerability Detection Challenge for Developers with New Automated Tool
This is a summary of a blog post published in full on NXP.com.
Connecting and being connected makes us vulnerable to hackers. With the number of IoT devices forecasted to reach 20.4 billion by 2020, the need for product security becomes even more pressing.
Every week, hundreds of new vulnerabilities are …
Full lifecycle security now available for Advantech’s new product line based on NXP i.MX 8 series processors
Designing secure products is important. But the ever-changing threat landscape means that a product may become vulnerable at any time after release. That’s why we are excited to announce a new offering for stronger security across the full embedded system product lifecycle with our partner, Advantech.
Now, product developers using Advantech platforms incorporating NXP i.MX applications processors will …
New security offering with NXP: Ensure embedded system security throughout product lifecycle
We are excited to announce a new collaboration with NXP® Semiconductors that enables product developers to maintain strong embedded system security throughout their product lifecycles.
The new offering combines our Timesys Vigiles Security Monitoring and Management Service with NXP processors to streamline and simplify security management.
CVE Monitoring & Management: Timesys’ Akshay Bhat Offers Security Guidance for Embedded Open Source Systems Part 2
As discussed in last week’s posting, central to the device maintenance process and keeping devices secure after they’ve been deployed is the ongoing monitoring and managing of CVEs that affect your product components. Therefore, it’s essential to have a clear view of relevant CVEs because there are many moving parts that need to be managed.
CVE Monitoring & Management: Timesys’ Akshay Bhat Offers Security Guidance for Embedded Open Source Systems Part 1
Timesys’ Director of Engineering, Akshay Bhat, presented a session on Open Source Security at the Embedded Linux Conference North America 2019 in August. For this two-part Q&A interview, our VP of Marketing Adam Boone asked Akshay to share his views on the challenges and best practices for maintaining security in Open Source Embedded System products.
Open Source CVE Monitoring and Management: Learn the Latest at Embedded Linux Conference 2019
Every week, more than 300 new vulnerabilities affecting software systems are disclosed by security reporting services such as the Common Vulnerabilities & Exposures (CVE) database operated by the US National Institute of Standards and Technology (NIST).
If you develop embedded systems or embedded devices, keeping pace with the constant flood of new vulnerabilities, knowing which directly affect …
Here comes the ‘stick’ for IoT security … or can we self-police?
Poor security of Internet of Things has led the US Federal Government to (again) consider legislation to force makers of IoT devices to improve security.
And the proposed bill comes on the heels of industry concern that IoT attacks against the US power grid are increasingly common and threaten public safety.
This week a bipartisan group of four US senators introduced the “Internet of Things (IoT) Cybersecurity ...
Is vulnerability management a regular part of your product management? (Spoiler alert: It better be.)
Effective product security starts with good product management.
And a good product manager recognizes that product security does not stop with secure design.
Effective security demands monitoring, tracking and acting on vulnerabilities on an ongoing basis …
Continuous Testing Delivers Quality with Faster Time-to-Market
System quality requirements have never been higher. But time-to-market pressures have also never been greater. How do you meet one without sacrificing the other?
Embedded systems users expect bug free, responsive and stable applications that provide the best user experience.
The consequence of failing to meet user expectations can result in more than just application abandonment. With the power of social media, it also can quickly lead to a …
The Risks of a ‘Stale, Abandoned’ Product
Some product management decisions are hard. Product managers are constantly weighing trade-offs among time-to-market, functionality, competitive differentiation, development costs and other factors.
But some product decisions seem like no-brainers. Would you bring an IT product to market that puts customers at significantly increased risk of security breaches, privacy violations, potentially massive fines and lawsuits?
“Of course not. That would be lunacy,” you can imagine the typical product manager as saying. Yet companies are shipping products every day that introduce this sort of …
Who is attacking IoT? What do they want?
The motivation of hackers sometimes can be plain as day. Other times, not so much.
As attacks on Internet of Things (IoT) devices and deployments escalate, it is important to understand what these attackers are trying to accomplish. Understanding these motives, after all, can help us to pinpoint why a security vulnerability represents a risk, to prioritize mitigation and defenses, and to focus responses to attacks.
This analysis is especially important if you provide products and platforms to companies deploying IoT …
New IDE version produces shorter time-to-market for secure IoT devices and embedded Linux applications
This week we announced a new release of our TimeStorm Integrated Development Environment (IDE). TimeStorm 5.3.2 IDE is designed to streamline, simplify and accelerate the development of secure Internet of Things (IoT) and embedded Linux applications.
In an era of heightened awareness of embedded software security and device security risks, product developers need to be able to adopt security best practices without delaying the development and release …
Ready to tackle embedded Linux MPU development with Windows … Do you know your options?
Have you been developing embedded devices for years? Are you considering building your first operating system based product and looking at using embedded Linux? You are not alone.
Many companies that have historically been developing MCU based products are now being pushed by market and customer requirements to offer better, more feature-rich and more capable devices. In order to deliver the desired features, many new designs require a …
Monitoring and managing vulnerabilities for embedded systems built with Yocto
The Yocto Project is well known for enabling product developers to quickly and easily customize Linux for Internet of Things (IoT) devices and other embedded systems. But today’s environment is marked by heightened security concerns, skyrocketing vulnerability reports, and high-profile security breaches.
Getting your embedded system product to market fast is important. But getting to market fast without a secure design and a plan for managing future vulnerabilities is a huge mistake.
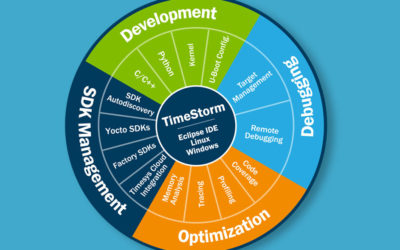
Why choose TimeStorm IDE over standard Eclipse for embedded Linux development?
As the product manager for TimeStorm, I am often asked the following two questions about TimeStorm, our Integrated Development Environment (IDE):
- Why would I need an integrated development environment?
- What can I do with TimeStorm that I can not do using Eclipse with available open source plugins?
There is no simple answer to these questions. Or is there?
Managing vulnerabilities: Understanding patch notifications and fixing CVEs
After Notification: The Next Steps
In a previous blog, we covered how Timesys handles security monitoring and notification of open source software vulnerabilities, how to generate reports on demand for the current state of a Yocto, Buildroot or Factory build on the desktop, and how to view and generate reports on the web. If you missed it, now would be a good time to catch up before reading this post, because the next steps cover what to do …
Managing vulnerabilities: The importance of security notification and how to leverage Timesys’ solution
Security Is Important
No matter what industry you’re in, maintaining the security of your software is vital. It may be obvious that medical devices need to protect patients and their privacy, but a range of consumer gadgets fueling the IoT have also been targeted and used to cause real damage.
Webinar: Building Embedded Software Efficiently with an IDE
Discover IDE-assisted software development best practices that can help you minimize the number of challenges you encounter and reduce development delays when building your value-add embedded application.
This four-session webinar series will utilize open source Linux and Timesys’ TimeStorm IDE for embedded application- and system-level development. You’ll see how TimeStorm provides a consistent development experience while providing application developers with the flexibility they need to be more efficient and productive.