Researchers and the technology media are reporting that the average application now contains more open source software components than proprietary code. And the use of open source components in embedded systems such as Internet of Things (IoT) devices likewise is on the rise.
How is this trend affecting awareness of embedded system security and open source security best practices? If you bring embedded system products to market with open source components, how do these systems affect your customers’ security postures?
To evaluate these questions, it helps to explore how enterprises test and measure the security of IT systems.
Enterprise Security Posture
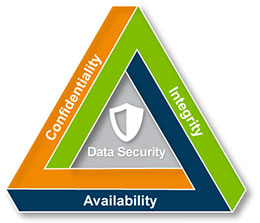
The security posture is a way to describe the aggregated effectiveness of security controls, processes and procedures. As we discussed in previous blog posts, many security practitioners use the acronym CIA as a rule-of-thumb for considering IT security. It stands for:
- Confidentiality — can the enterprise protect data and keep it private?
- Integrity — can the enterprise ensure data is not altered or manipulated?
- Availability — can the enterprise make sure that data is available and accessible when it is needed?
Sometimes security practitioners refer to the “A” in CIA as Authentication, or Access, but the fundamental meaning is closely related across all the terms, that the enterprise is able to provide access to the information to authorized users who need it, when they need it.
CIA Triad
Different enterprises will address the CIA requirements in different ways, depending on the industry and regulatory environment they operate in. For example, a hospital system in the United States operates under strict federal laws that require it to protect patient data from disclosure to unauthorized people. So such an enterprise is likely to invest heavily in encryption and similar confidentiality oriented technologies.
Penetration Testing and Security Assessments
The process of planning and implementing a security posture can be lengthy and complex. At even a modest sized enterprise, many systems may be involved in the collection, processing, communication and storage of sensitive data. As a result, there are many cases in which security gaps or vulnerabilities are not identified until a successful attack has taken place. The famous Target breach of a few years ago took place only three months after the company had passed a credit card security audit.
Waiting until a breach takes place to discover potential vulnerabilities in your security posture is of course a disaster in the making. So, many enterprises, especially those in industries like finance and healthcare where security is mission critical, will periodically conduct thorough security testing that often includes penetration testing.
A penetration test is exactly what it sounds like. The company assigns IT experts — often external consultants who specialize in such tests — to see if they can penetrate the IT security defenses and break into the company’s systems, access data, manipulate systems and devices, and otherwise compromise the intended security posture.
If you make products that are used in sensitive environments and contexts, such as devices involved in medical diagnosis or treatment, processing of consumer data or financial transactions, transportation, industrial and so on, then it is important to realize that your systems are targets in these hacking exercises.
Penetration Testing and Security Assessments
Embedded Linux security has received a lot of attention as embedded open source systems have become increasingly widespread.
It’s important that developers consider Internet of Things device security and embedded system security for open source software as they relate to the overall security needs of the enterprises who eventually will deploy those systems.
This is accomplished with device security auditing, which is similar to penetration testing in the sense that it seeks to evaluate the security of the device and its embedded systems as viewed from the potential attacker’s point of view. An audit could consider questions such as:
- Are the device’s software components updated with the latest versions?
- Is the configuration of the systems appropriate to the application and the eventual deployment mode of the device?
- Have any Common Vulnerabilities and Exposures (CVEs) been released that pertain to the systems and components in the device?
Conducting this type of security risk assessment for your device before it is released on the market, and periodically whenever updates are prepared for release, can go a long way toward making sure the device does not expose vulnerabilities or flaws that can put your customers at risk of a data breach.
An audit also can uncover issues that should be addressed as part of a device hardening project, a critical stage of product development that considers how much damage an attacker could do if they succeeded in exploiting a vulnerability and taking control of the device.
Our Secure by Design offering includes security audits and device hardening to ensure security is baked into your products early in their development. The audit service includes a detailed review of software packages and your system’s default configuration. It can provide analysis of vulnerability reports from scanning tools as well as a risk management and recovery plan.
Our TRST (Threat Resistance Security Technology) Product Protection Solutions also help to maintain your product’s security posture into the future.
The CVE monitoring and notification service enables you to understand and respond to the appropriate CVE notifications that affect your products. At Timesys we help device developers to address embedded system IoT security across a wide range of device types.
Contact us to learn more.
About Timesys
Timesys has extensive experience with embedded system development and lifecycle management. Timesys has been instrumental in working with global leader semiconductor manufacturers with smart, quick and quality solutions for highly complex systems with accelerated product innovation and multiple product variants.


